ETR Insights presents an interview with the Cyber Attack Response Engineer for a global financials enterprise. Readers will appreciate this informed perspective on platform-style security solutions, ZTNA, endpoint updates and sensor-based security technologies, and cost-efficient log management. The discussion turned quickly to security vendors, including Cloudflare, Tanium, CrowdStrike, Okta, Ping, SailPoint, and more within the space, and offers particular insight into Palo Alto’s perceived strengths over Cisco, and Zscaler’s capacity to service multiple industry verticals.
Vendors Mentioned: Absolute Technologies / AWS / Auth0 / Cisco / Cloudflare / CrowdStrike / Dynatrace / Elastic / Fortinet / Juniper / Microsoft / Okta / Oracle / Palo Alto / Ping / SentinelOne / Tanium / Zscaler
IT Spending Overview
IT budgets in larger companies have grown in part due to the purchase of laptops, following the shift to remote work; spend on VPN technologies that enable restricted access to corporate networks and data is in tandem. Zero trust network access, identity management, and endpoint security have come into focus. “Another growth area that we’re seeing take a huge uptick in is AWS WorkSpaces and virtualization. You can actually place in the cloud technology as far as your own homegrown software and information technologies that you’ve cooked up in-house.” These services are now widespread and affordable, and smaller, more nimble companies are quickly adopting them. “Larger companies like us, where we employ 90,000 people worldwide, it’s more slow-moving because of the astronomical cost that it’s going to be to move into that space.”
Vendor-Specific Commentary – Enterprise Security
Zscaler. The organization selected Zscaler for zero trust network access, supplemented by Absolute Technologies’ “endpoint lockdown measures,” which allow for immediate lockdown upon breach or termination. Zscaler offers our guest top-notch support, even creating internal videos to assist the company’s technologists. Pricing is satisfactory, but Zscaler does face significant challenges in catering to different business verticals with specific regulations. “Whether it be healthcare, financial, aerospace and development, or engineering services, all of which we kind of work in, we have to have the flexibility to restrict within and comply with the specific regulations related to that business vertical.” Another drawback is the slow process to add specific websites or portals to the system. “In the current scope that we have right now, that’s usually days, if not weeks, to be able to get something whitelisted.”
Cloudflare + platform solutions. The conversation turned to other companies in the security industry that offer platform-style solutions, including Fortinet, Palo Alto, Cisco, Microsoft, and Cloudflare. Our guest is presently helping a client integrate FortiClient VPN within Zscaler as their endpoint security solution; they are hopeful that Cloudflare, who continues to roll out new offerings, may be able to provide a custom solution that fits all the client’s security needs and cover all the services and portals that are currently whitelisted within Zscaler.
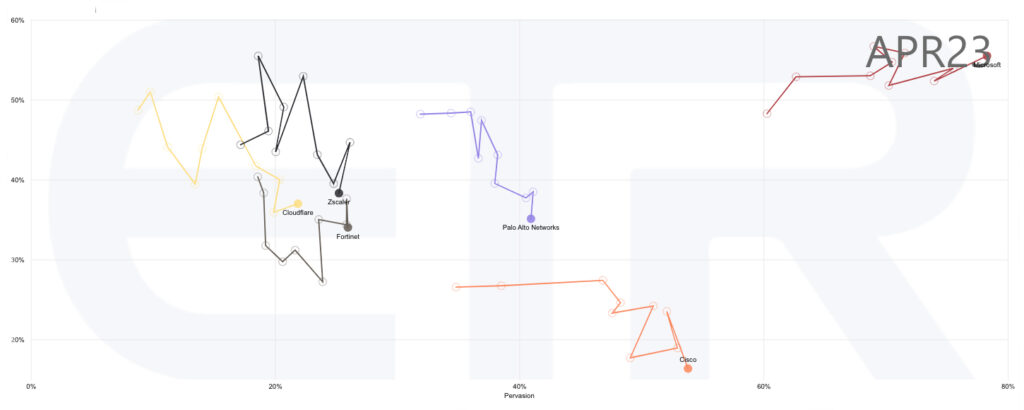
Palo Alto. Palo Alto and Cisco were originally known for hardware, but are now making the transition to software and services through acquisitions and internal R&D. Our guest particularly admires Palo Alto. “The lead engineers actually came over from Cisco, so you have a lot of the similar flavor and feel with Palo Alto, but their price point is probably one third of what Cisco is, and the quality is as good” While they still use Cisco routing and switching, this organization has moved away from Cisco firewalls and Juniper Networks’ VPN to Palo Alto. “Palo Alto is reinvesting and growing in that space at a better pace than Cisco.”
Tanium + CrowdStrike. This industry specialist uses Tanium to update endpoints as soon as they connect to the Internet, and appreciates CrowdStrike’s cloud-based, sensor-based technology for 24/7 security. “[CrowdStrike] is sensor-based technology, rather than if you think of the old days of Norton Security. It’s more of a learning and adaptive type of an environment for security.” This eliminates the need for manual updates and patching, allowing organizations to focus on growing their business and keeping their customers safe.
Vulnerability management. CrowdStrike, SentinelOne, and Tanium hope to replace traditional vulnerability management, though our guest wants to see a more proven track record before adopting. “I think eventually, probably within the next 6 to 12 months, companies around the globe are going to be looking at something like this. The less IT spend we’re having, that’s more that we can put into bottom-line profits and growing other areas of the company.” CrowdStrike already offers patching similar to Tenable’s offerings, but Tanium is particularly helpful to address patches and updates across disparate vertical segments. “We’re looking for CrowdStrike to say, ‘Here’s what we can do, our white papers and some of the case studies that we’ve done over the last three to six months.’ And we’re going to say, okay.”
Elastic. This engineer uses Elastic for log management but expresses an interest in seeing other players compete in the space. Re-analyzing Elastic and other vendors yearly to assess their service and audit-readiness is cumbersome; our guest would love it if “somebody else could come along, that has the certifications, that can partner with us and measure the specific logging and information, as well as the backup and recovery that’s going to be required.” According to our guest, Dynatrace is similarly “resting on their laurels from the past.”
Okta, SailPoint + Ping. Okta provided this organization with a nimble solution for integrating existing Active Directory services during the pandemic. “They were able to move to Azure technologies with Microsoft, so we could implement that and make those all come together.” Our guest expressed frustration with SailPoint; however, who struggled to adapt to the company’s need for multiple subdomains. For identity management, the company uses a combination of in-house resources, such as Okta, and Ping Identity. For our guest, Ping’s expertise in aerospace, defense, and government contracts make them a strong partner.
